Nmap 6.47
Nmap 6.47
Gordon Lyon - ( Open Source)
Nmap is a powerful and indispensable tool for all network administrators developed to explore and perform an audit or a computer network hardware inventory.
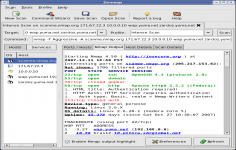
Nmap ("Network Mapper") is a software application that allows to detect open ports as well as information on a remote computer. Network administrators can use to identify the network status, manage schedules update services and monitor the availability of each item.
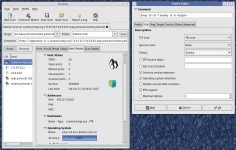
Using uses TCP, ICMP, IP or UDP it identifies services hosted on a computer. Thus, information such as the operating system or available ports can be accessed. Specific reports also allow to perform a specific audit of the safety and security of the system.
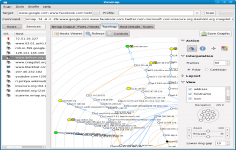
The functional graphical user interface provides access to a wealth of information at the first glance.
- Title:
- Nmap 6.47
- File Size:
- 25.9 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / XP64 / Vista64 / Windows7 64 / Windows8 / Windows8 64
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 25 Aug 2014
- Publisher:
- Gordon Lyon
- Homepage:
- http://nmap.org
- MD5 Checksum:
- E5DE516447B9A36029273694EA49B0C7
- Integrated all of your IPv4 OS fingerprint submissions since June 2013. Added 366 fingerprints, bringing the new total to 4485. Additions include Linux 3.10 - 3.14, iOS 7, OpenBSD 5.4 - 5.5, FreeBSD 9.2, OS X 10.9, Android 4.3, and more. Many existing fingerprints were improved.
- (Windows, RPMs) Upgraded the included OpenSSL to version 1.0.1i.
- (Windows) Upgraded the included Python to version 2.7.8.
- Removed the External Entity Declaration from the DOCTYPE in Nmap's XML. This was added in 6.45, and resulted in trouble for Nmap XML parsers without network access, as well as increased traffic to Nmap's servers.
- [Ndiff] Fixed the installation process on Windows, which was missing the actual Ndiff Python module since we separated it from the driver script.
- [Ndiff] Fixed the ndiff.bat wrapper in the zipfile Windows distribution, which was giving the error, "\Microsoft was unexpected at this time.
- [Zenmap] Fixed the Zenmap .dmg installer for OS X.
- [Ncat] Fixed SOCKS5 username/password authentication. The password length was being written in the wrong place, so authentication could not succeed.
- Avoid formatting NULL as "%s" when running nmap --iflist. GNU libc converts this to the string "(null)", but it caused segfault on Solaris.
- [Zenmap][Ndiff] Avoid crashing when users have the antiquated PyXML package installed. Python tries to be nice and loads it when we import xml, but it isn't compatible. Instead, we force Python to use the standard library xml module.
- Handle ICMP admin-prohibited messages when doing service version detection.
- [NSE] Fix a bug causing http.head to not honor redirects.
- [Zenmap] Fix a bug in DiffViewer causing this crash: TypeError: GtkTextBuffer.set_text() argument 1 must be string or read-only buffer, not NmapParserSAX Crash happened when trying to compare two scans within Zenmap.