TrueCrypt 5.1a
TrueCrypt 5.1a
TrueCrypt Foundation - (Open Source)
Encrypting a USB key or a whole disk or even creating virtual encrypted disks, all these are possible with TrueCrypt.
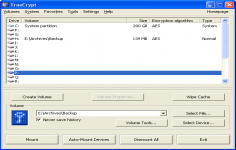
TrueCrypt is a solution for storing encrypted information, allowing to create encrypted virtual disks. When mounted, the media appear in Explorer as a local disk. The application is also able to encrypt an entire volume or partition, which is very useful if there are sensitive information on the USB drive, for example. The encrypted volume is seen by the system as a typical hard and has all the features, being necessary only to enter the password associated with the volume at the time of "montage".
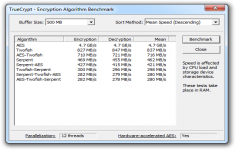
The software also includes hardware acceleration for encryption and decryption of AES algorithm. Enabled by default , this small revolution concerns only the recent Intel processors with the necessary capabilities : Intel Core i7- 980X , Intel Core i7 -970 , Intel Core i5- 650, Intel Core i5- 655K , Intel Core i5- 660, Intel Core i5 -661 , Intel Core i5 -670 , Intel Core i5 -680 and more, the speed of encoding and decoding being up to 8 times faster.
A volume can be mounted directly under Windows subject to provide the correct password. It is possible to create partitions and storage devices encrypted on the hard disk sectors with 4096, 2048 or 1024 bytes.
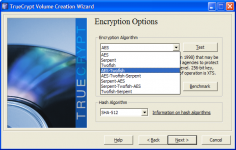
Many standard algorithms are supported by TrueCrypt, such as AES-256, Blowfish, CAST5, Serpent, Triple DES, and Twofish.
- Title:
- TrueCrypt 5.1a
- File Size:
- 2.5 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / XP64 / Vista64 / Windows7 64 / Windows8 / Windows8 64
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 16 Mar 2008
- Publisher:
- TrueCrypt Foundation
- Homepage:
- http://www.truecrypt.org
- MD5 Checksum:
- 0B02B6A8B9437F8968CBE8719722079B
Improvements:
* Faster booting when the system partition/drive is encrypted (typically by 10%). (Windows Vista/XP/2008/2003)
* Other minor improvements. (Windows, Mac OS X, and Linux)
Resolved incompatibilities:
* On computers with certain hardware configurations, resuming from hibernation failed when the system partition was encrypted. Note: If you encountered this problem, the content of RAM may have been saved unencrypted to the hibernation file. You can erase such data, for example, by decrypting the system partition/drive (select System > Permanently Decrypt System Partition/Drive) and then encrypting it again. (Windows Vista/XP/2008/2003)
Remark: As Microsoft does not provide any API for handling hibernation, all non-Microsoft developers of disk encryption software are forced to modify undocumented components of Windows in order to allow users to encrypt hibernation files. Therefore, no disk encryption software (except for Microsoft's BitLocker) can guarantee that hibernation files will always be encrypted. At anytime, Microsoft can arbitrarily modify components of Windows (using the Auto Update feature of Windows) that are not publicly documented or accessible via a public API. Any such change, or the use of an untypical or custom storage device driver, may cause any non-Microsoft disk encryption software to fail to encrypt the hibernation file. We plan to file a complaint with Microsoft (and if rejected, with the European Commission) about this issue, also due to the fact that Microsoft's disk encryption software, BitLocker, is not disadvantaged by this.
* Workaround for a bug in the BIOS of some Apple computers that prevented users from entering pre-boot authentication passwords and controlling the TrueCrypt Boot Loader. (Windows Vista/XP/2008/2003)
Bug fixes:
* When the system partition/drive is decrypted under Windows, the original partition table will not be restored. Note: This issue affected users who repartitioned an encrypted system drive and then decrypted it under Windows. (Windows Vista/XP/2008/2003)
* Other minor bug fixes. (Windows, Mac OS X, and Linux)
Related software
2.7/5 from 107 users