TrueCrypt 6.0
TrueCrypt 6.0
TrueCrypt Foundation - (Open Source)
Encrypting a USB key or a whole disk or even creating virtual encrypted disks, all these are possible with TrueCrypt.
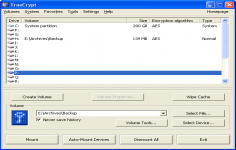
TrueCrypt is a solution for storing encrypted information, allowing to create encrypted virtual disks. When mounted, the media appear in Explorer as a local disk. The application is also able to encrypt an entire volume or partition, which is very useful if there are sensitive information on the USB drive, for example. The encrypted volume is seen by the system as a typical hard and has all the features, being necessary only to enter the password associated with the volume at the time of "montage".
The software also includes hardware acceleration for encryption and decryption of AES algorithm. Enabled by default , this small revolution concerns only the recent Intel processors with the necessary capabilities : Intel Core i7- 980X , Intel Core i7 -970 , Intel Core i5- 650, Intel Core i5- 655K , Intel Core i5- 660, Intel Core i5 -661 , Intel Core i5 -670 , Intel Core i5 -680 and more, the speed of encoding and decoding being up to 8 times faster.
A volume can be mounted directly under Windows subject to provide the correct password. It is possible to create partitions and storage devices encrypted on the hard disk sectors with 4096, 2048 or 1024 bytes.
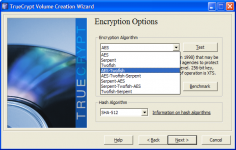
Many standard algorithms are supported by TrueCrypt, such as AES-256, Blowfish, CAST5, Serpent, Triple DES, and Twofish.
- Title:
- TrueCrypt 6.0
- File Size:
- 3.0 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / XP64 / Vista64 / Windows7 64 / Windows8 / Windows8 64
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 04 Jul 2008
- Publisher:
- TrueCrypt Foundation
- Homepage:
- http://www.truecrypt.org
- MD5 Checksum:
- EC0827315825A035FF9A4203DDDDFEF7
New features:
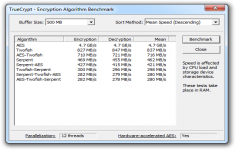
*Parallelized encryption/decryption on multi-core processors (or multi-processor systems). Increase in encryption/decryption speed is directly proportional to the number of cores and/or processors.
For example, if your computer has a quad-core processor, encryption and decryption will be four times faster than on a single-core processor with equivalent specifications (likewise, it will be twice faster on dual-core processors, etc.)
[View benchmark results]
*Ability to create and run an encrypted hidden operating system whose existence is impossible to prove (provided that certain guidelines are followed). For more information, see the section Hidden Operating System. (Windows Vista/XP/2008/2003)
For security reasons, when a hidden operating system is running, TrueCrypt ensures that all local unencrypted filesystems and non-hidden TrueCrypt volumes are read-only. (Data is allowed to be written to filesystems within hidden TrueCrypt volumes.)
Note: We recommend that hidden volumes are mounted only when a hidden operating system is running. For more information, see the subsection Security Precautions Pertaining to Hidden Volumes.
*On Windows Vista and Windows 2008, it is now possible to encrypt an entire system drive even if it contains extended/logical partitions. (Note that this is not supported on Windows XP.)
*New volume format that increases reliability, performance and expandability:
o Each volume created by this or later versions of TrueCrypt will contain an embedded backup header (located at the end of the volume). Note that it is impossible to mount a volume when its header is damaged (the header contains an encrypted master key). Therefore, embedded backup headers significantly reduce this risk. For more information, see the subsection Tools > Restore Volume Header.
Note: If the user fails to supply the correct password (and/or keyfiles) twice in a row when trying to mount a volume, TrueCrypt will automatically try to mount the volume using the embedded backup header (in addition to trying to mount it using the primary header) each subsequent time that the user attempts to mount the volume (until he or she clicks Cancel). If TrueCrypt fails to decrypt the primary header and then decrypts the embedded backup header successfully (with the same password and/or keyfiles), the volume is mounted and the user is warned that the volume header is damaged (and informed as to how to repair it).
o The size of the volume header area has been increased to 128 KB. This will allow implementation of new features and improvements in future versions and ensures that performance will not be impaired when a TrueCrypt volume is stored on a file system or device that uses a sector size greater than 512 bytes (the start of the data area will always be aligned with the start of a host-filesystem/physical sector).
For more information about the new volume format, see the section TrueCrypt Volume Format Specification.
Note: Volumes created by previous versions of TrueCrypt can be mounted using this version of TrueCrypt.
* Parallelized header key derivation on multi-core processors (one algorithm per core/thread). As a result, mounting is several times faster on multi-core processors. (Windows)
*Ability to create hidden volumes under Mac OS X and Linux.
*On Linux, TrueCrypt now uses native kernel cryptographic services (by default) for volumes encrypted in XTS mode. This increases read/write speed in most cases. However, the FUSE driver must still be used when the volume is encrypted in a deprecated mode of operation (LRW or CBC), or when mounting an outer volume with hidden-volume protection, or when using an old version of the Linux kernel that does not support XTS mode. (Linux)
Improvements:
*Up to 20% faster resuming from hibernation when the system partition/drive is encrypted. (Windows Vista/XP/2008/2003)
*Many other improvements. (Windows, Mac OS X, and Linux)
Removed features:
*Encrypted system partitions/drives can no longer be permanently decrypted using the TrueCrypt Boot Loader (however, it is still possible using the TrueCrypt Rescue Disk). (Windows Vista/XP/2008/2003)
Note: This was done in order to reduce the memory requirements for the TrueCrypt Boot Loader, which was necessary to enable the implementation of support for hidden operating systems.
Bug fixes:
*When Windows XP was installed on a FAT16 or FAT32 partition (as opposed to an NTFS partition) and the user attempted to encrypt the system partition (or system drive), the system encryption pretest failed. This will no longer occur.
*Many other minor bug fixes and security improvements (preventing e.g. denial-of-service attacks). (Windows, Mac OS X, and Linux)
Related software
2.8/5 from 103 users