Wireshark 1.0.3
Wireshark 1.0.3
Wireshark.org - (Open Source)
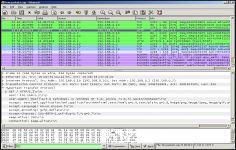
Wireshark helps network administrators to solve protocol issues by diagnosing the problems in the software protocols.
Wireshark is a famous network analysis or packet sniffer tool protocols.
Wireshark examine data from a live network, and can also take a snapshot of the various communications that work on it at another time. Wireshark proposes to see the "dissector tables" directly from the main window. The application can export objects to SMB screen or display the compiled BPF code for capture filters. Finally, Wireshark supports a variety of protocols such as ADwin, Apache Etch, JSON, reload or Wi-Fi P2P (Wi-Fi Direct).
The interface is quite austere, hides an extremely powerful that only experts can use software correctly.
This software is essential for any network administrator to diagnose problems in the software protocols.
- Title:
- Wireshark 1.0.3
- File Size:
- 21.2 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / Windows8
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 04 Sep 2008
- Publisher:
- Wireshark.org
- Homepage:
- http://www.wireshark.org/
- MD5 Checksum:
- 980F7AA115A40D1DD563C39FDC69D55A
Notes:
Wireshark 1.0.3 Release Notes
------------------------------------------------------------------
What is Wireshark?
Wireshark is the world's most popular network protocol analyzer.
It is used for troubleshooting, analysis, development, and
education.
What's New
Bug Fixes
The following vulnerabilities have been fixed. See the security
advisory for details and a workaround.
o The NCP dissector was susceptible to a number of problems,
including buffer overflows and an infinite loop.
Versions affected: 0.9.7 to 1.0.2
o Wireshark could crash while uncompressing zlib-compressed
packet data.
Versions affected: 0.10.14 to 1.0.2
o Wireshark could crash while reading a Tektronix .rf5 file.
Versions affected: 0.99.6 to 1.0.2
The following bugs have been fixed:
o 802.11 WPA/WPA2-PSK Unable to decode Group Keys. (Bug 1420)
o Packets could wrongly be dissected as "Redback Lawful
Intercept" (Bug 2376)
o MIKEY dissector improvements (Bug 2400)
o tvb_get_bits{16|32} could read past the end of a tvbuff (Bug
2439)
o Incorrect wslua function names. (Bug 2448)
o Memory corruption in wslua. (Bug 2453)
o Unknown PPPoE TAGs which are present in a PPPoE discovery
packet are not displayed under "PPPoE Tags" subtree/section.
(Bug 2458)
o Following a TCP stream could incorrectly reassemble packets.
(Bug 2606)
o SIP decode shows fully expanded "Content-Length" header
instead of compact form. (Bug 2635)
o Segmentation fault loading trace containing NCP packets. (Bug
2675)
o SIP packets might incorrectly be displayed as malformed. (Bug
2729)
o RTCP BYE padding interpreted incorrectly. (Bug 2778)
o Reversed RTP stream is saved as silent .au file, forward
stream saves correctly. (Bug 2780)
o Fix some lint warnings. (Bug 2822)
o Setting a duration on a capture file would capture for an
extra second.
New and Updated Features
There are no new or updated features in this release.
New Protocol Support
There are no new protocols in this release.
Updated Protocol Support
AIM, Bluetooth RFCOMM, ERF, K12, NCP, PPP BCP, PPPoE, Q.933,
Redback LI, RTCP, RTP, SIP, SNMP, TCP, V.120, WiMAX
New and Updated Capture File Support
Endace ERF.
Getting Wireshark
Wireshark source code and installation packages are available from
the download page on the main web site.
Vendor-supplied Packages
Most Linux and Unix vendors supply their own Wireshark packages.
You can usually install or upgrade Wireshark using the package
management system specific to that platform. A list of third-party
packages can be found on the download page on the Wireshark web
site.
File Locations
Wireshark and TShark look in several different locations for
preference files, plugins, SNMP MIBS, and RADIUS dictionaries.
These locations vary from platform to platform. You can use
About->Folders to find the default locations on your system.
Known Problems
Wireshark may appear offscreen on multi-monitor Windows systems.
(Bug 553)
Wireshark might make your system disassociate from a wireless
network on OS X. (Bug 1315)
Dumpcap might not quit if Wireshark or TShark crashes. (Bug 1419)
The BER dissector might infinitely loop. (Bug 1516)
Wireshark can't dynamically update the packet list. This means
that host name resolutions above a certain response time threshold
won't show up in the packet list. (Bug 1605)
Capture filters aren't applied when capturing from named pipes.
(Bug 1814)
Wireshark might freeze when reading from a pipe. (Bug 2082)
Capturing from named pipes might be delayed on Windows. (Bug 2200)
Filtering tshark captures with display filters (-R) no longer
works. (Bug 2234)
Getting Help
Community support is available on the wireshark-users mailing
list. Subscription information and archives for all of Wireshark's
mailing lists can be found on the web site.
Commercial support and development services are available from
CACE Technologies.
Frequently Asked Questions
A complete FAQ is available on the Wireshark web site.
Related software
4.2/5 from 54 users